Security concerns are incredibly common and have the potential to wreak huge damages to a site and its long-term organic performance
Exactly why is cybersecurity important for SEO?
If you’re working closely with a website – for an agency, independently, or in-house – it’s likely you’ve been confronted with a security issue at some point. Though they range in threat-level, security concerns are incredibly common and have the potential to wreak huge damages to a site and its long-term organic performance.
Despite the ubiquitous threat, it seems digital marketers rarely feel the need to delve too deeply into the security space. Many believe it is simply not in their remit or not their problem.
As strategies for SEO and cyber attacks have evolved side-by-side, it’s become clear that security is something that digital marketers need to actively pay attention to. An effective SEO consultant must be well-versed enough to inform their clients on best practices.
Download our Premium Resource – A guide to developing digital skills in your agency
If your agency has a skills gap, then this is both a threat and an opportunity for your agency. A threat if you don’t address it but an opportunity if you put together a skills development plan for the agency and get ahead of your competition.
Access the A guide to developing digital skills in your agency
How will security affect my rankings?
Research shows that most websites will experience an average of 58 attacks per day. As much as 61% of all internet traffic is automated – meaning these attacks do not discriminate based on the size or popularity of the website in question. No site is too small or too insignificant to attack.
Aside from the direct financial loss, a compromised website can result in dramatic traffic implications, distorted SERPs and a range of manual penalties from Google. That’s not to mention the other repercussions; stolen information, compromised databases and potentially de-indexing.
It’s easy to grow complacent and trust Google to flag your site should it be affected. The truth is, search engines are flagging only a fraction of the total number of websites infected with malware. In the remaining cases, the operator continues its activity as usual while attackers take advantage of an open vulnerability.
Not only will this increase the severity of sanctions eventually imposed, gradual changes to your site content, relevancy and architecture will affect your rankings in the meantime. The crucial lesson is this: don’t rely on Google to consistently detect malware.
In other cases, Google may misinterpret activity from a compromised site as a deliberate attempt at cloaking. This can happen on a client’s existing domain, or even on a previous domain that 301-redirects to their current site. Both will result in manual penalties.

This is especially alarming considering that 9%, or as many as 1.7 million websites, have a major vulnerability that could allow for the deployment of malware. If you’re invested in your long-term search visibility, operating in a highly competitive market, or heavily reliant on organic traffic, vigilance in preventing attacks is crucial.
It’s clear that every effective SEO should be taking some responsibility for site security. If a client has the appropriate tools, resources, and strategies in place, great. But this is often not the case; very few ever deem website security an urgent concern that warrants immediate attention. Likewise, despite its direct impact on their performance, digital marketers often see it as a remote issue outside of their job spec.
Cybersecurity is a complex and multifaceted issue; it can be difficult to know where to start. In this article, we’ll cover some simple strategies for performing basic web security checks with search performance in mind, as well as various resources that can help you further your skillset and get to grips with the basics of website security.
Stages of an attack
In order to identify and respond to attacks, we first need a basic understanding of how they operate. Keep in mind, this assumes the attack is targeted rather than the result of indiscriminate scans. A typical attempt at compromise will have five stages:
- Reconnaissance. The attacker gathers as much information about the website as possible. This includes the software your site runs on, plugins, extensions, etc.
- Scanning. The website is scanned in an attempt to identify potential vulnerabilities.
- Forcing entry. Taking advantage of any given weakness, the attacker gains access to the site’s back-end.
- Securing entry. Once in, any smart attacker will ensure a backdoor entry-point is available for future access. This can often be exploited even after a site has been 'fixed'.
- Masking activity. The attacker will attempt to cover their tracks to ensure their presence remains undetected for as long as possible.
When trying to secure your site, you can identify vulnerabilities using the same methods as a malicious actor would.
The easiest way to avoid a compromise is to make the preliminary phases difficult; offer as little information about your site and its infrastructure as possible, so those with ill intentions have a much harder time identifying points of access. This will deter the majority of targeted attempts and make automated attacks much more difficult.
Server and CMS varieties
Most attackers will begin reconnaissance by identifying what software the site runs on. Popular software is routinely patched to cover new vulnerabilities, so if your site runs on an outdated version of a given platform, it’s much easier to compromise.
This is also arguably the easiest piece of information to discover. There are multiple ways to do this; online scanners like BuiltWith or WhatWeb will tell you exactly what software and which version powers a given domain.
Once you know this, you should find out what the latest version of the software package is. If you’re using the most recent version, that’s fine. If you’re running an outdated version, it’s sensible to check if there have been any notable vulnerabilities patched in the space between your current version and the latest release.
WordPress exploits
As the most commonly-used CMS on the web, WordPress is regularly targeted by attackers. It’s vital you know how to carry out basic security checks on sites reliant on the platform and that you’re capable of advising clients on WordPress security best practice in general. If you don’t, their site – and their SEO – is vulnerable in the long-run.
The vast majority of basic WordPress attacks are due to poor login security. If you’re using standard usernames – or your administrator username is still 'admin' – you’re running a risk.
It’s also worth changing your site’s login URL. The standard URL ('wp-login.php') will be the default URL used by automatic vulnerability scanners.
Overall, the best way to begin approaching WordPress security is to use a security plugin which, if kept updated, will help monitor and protect your site. These tools have a range of features designed to streamline your site’s security. Go through the settings to make sure your website has at least the basic features enabled.
Popular examples include All in One and Sucuri Security, which monitor and scan for potential hacking events and have firewall features that block suspicious visitors on a permanent basis.
Ultimately, it’s important to review, research and update each plugin and script you use. It’s better to invest the time in keeping your plugins updated than make yourself an easy target.
Login folder
Even if your site doesn’t rely on WordPress, that doesn’t mean it won’t be targeted. A custom or proprietary platform can still fall victim to an attack if you’re not following basic security protocols.
For example, it’s fairly simple for someone to find your website’s login URL, which serves as the perfect target for any attacker.
Many websites overtly block the back-end login folder in their robots.txt file. This might look something like the following:
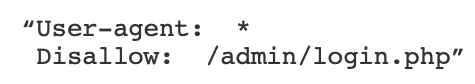
Given this is a publicly available file, this amounts to broadcasting your login URL to anyone looking to force their way into your website.
Even if you’ve got this covered, another simple Google search can often provide a hacker with this information:
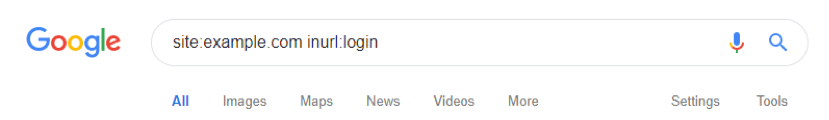
A 'site:' search for URLs with 'login' or 'admin' in them can easily turn up a login page that’s been indexed. Ensure your robots.txt doesn’t give this away and use 'noindex' meta tags on your login pages to prevent them being accidentally indexed.
Shared hosting
Small websites often exist on shared hosting servers. In this case, your site’s security is only as good as the most poorly secured website on the server. If an attacker compromises one, they’re more likely to access the entire server and every site therein.
If you’re unsure, simple tools like SpyOnWeb can help you find out if a particular site is hosted on a shared server. Just input the website’s domain and you’ll get a quick overview of all other domains associated with the same IP address. If these do not all share the same owner, the website is part of a shared hosting server.
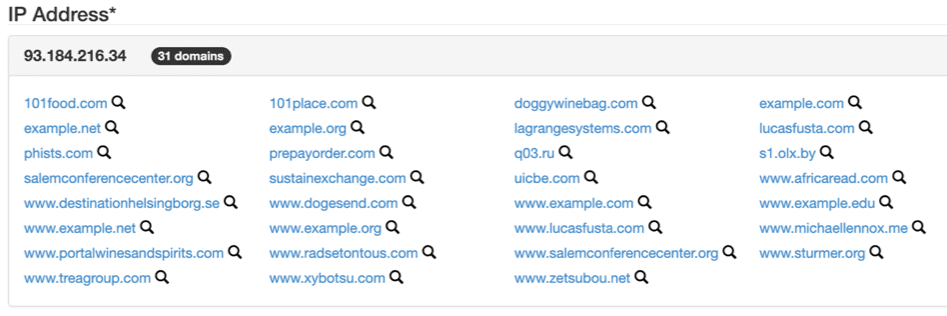
Shared hosting is essentially equivalent to putting your website’s safety in the hands of the least capable webmaster on the server.
Typically, dedicated hosting is the way to go. Depending on the vulnerability and volume of sensitive data on your site, it’s wise to migrate to a dedicated server as soon as possible.
Google hacking
In many cases, finding exposed information about a site is as easy as typing the query into Google. With some simple searches, you can find a lot of interesting things; log files, configuration files, indexed PDF documents, SQL error messages (which indicate potential vulnerabilities) and much more.
Websites like PenTest-Tools offer assistance in counteracting this form of reconnaissance. Once you’ve entered your domain name, the tool will pair it with queries such as "directory listing vulnerabilities", "SQL errors", "log files exposed", and many more.
If you can find information on your site from these queries, attackers can too. Subject your site to every one of these searches and work to remove the source of any information that’s readily available.
Aside from "google hacking", there are plenty of tools available online that you can use to collect certain types of information, including a domain’s open TCP ports, active subdomains, SSL vulnerabilities and more. It’s worth doing your research here; you and your client should know exactly what information is exposed that could be used to inform an attackers strategy.
SSL updates
HTTPS is important, but it doesn’t necessarily mean you have a secure website. It’s easy to forget that not all SSL certificates are the same.
In recent years, there have been various scares surrounding weaknesses in SSL, most notably the DROWN and Heartbleed attacks. Generally speaking, it’s worth investing in a high-grade certificate that’s fully up to date and has no known susceptibilities. If you’re unsure, you can use the SSL Labs tool to test the quality of the certificate on a certain site.
It’s wise to test your certificate regularly to stay in line with the latest vulnerabilities.
Scanning software
What’s been covered so far will do enough to maintain basic web security and discourage amateurs or automated tools. If you’re targeted by a dedicated attacker, you might not fare so well; there could be a whole host of further vulnerabilities buried in your site.
Tools like Nikto web scanner are free, easily available and will test your site against thousands of known issues. This is a command prompt tool you can download and run yourself; it will run on most PCs though it’s most commonly used on Linux. If you’re not comfortable running the software yourself, there are lots of tools available online that will perform the scan for you.
The bottom line
This article covers some preliminary steps you can use to find common security issues in a website. Holistic cybersecurity is a much larger field composed of multiple specialties, of which website security is just a small area.
SEO is – and has always been – about embracing change. If you want to offer the best service possible and improve your results in the long run, you must learn to adapt to shifting requirements in the field.
Security issues are not going away any time soon. Given their impact on the overall user experience, it’s likely their impact on SEO is only set to grow. Invest in your education now and it will undoubtedly pay off – for you and your clients – in the long-run.
William Chalk is a security researcher at
Top10VPN, a cybersecurity research group and the world’s largest VPN review service. Top10VPN has been recognized by leading publications around the world for their advocacy of digital privacy and security rights.